I travel 200,000 miles a year, talking to CIOs and CISOs all over the world. While I encounter a wide range of issues relating to the security posture and maturity of these organizations, the one theme that resonates with them all is a conversation around focusing on the “big rocks”.
Too often, the people responsible for cybersecurity get mired in a discussion about all the ways an attacker can potentially get data from your company. We can get trapped in a daily tactical battle to scour through false alarms or resolve the compromises of a user device or their credentials. The problem is that we are not able to see the whole forest through all the trees.
Senior managers are often recognized for their ability to see the big picture and focus on the big rocks.
So, what are these big rocks?
- The Map: It may seem straight-forward, but many companies that have extensive applications, data, and devices do not have a map of their business-critical assets, zones, or users. Being able to locate, categorize, and prioritize your assets is a first step to defining risk, and implementing defense in depth, threat monitoring, and threat response.
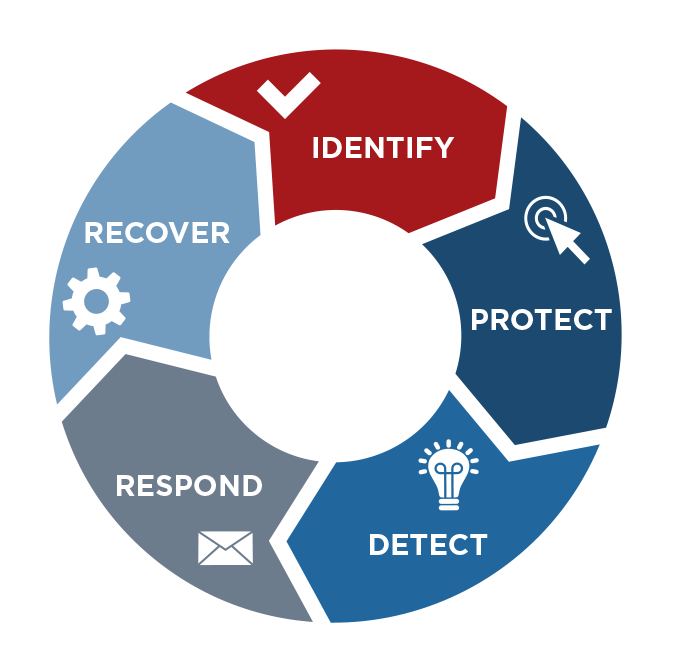
The NIST Framework prescribes a set of activities that help companies to achieve cybersecurity outcomes. - The Holes: If you have a leaky boat, the priority is patching the holes that are letting in the most water. The same goes for cybersecurity. Although this seems simple, most companies are not applying a risk-based approach to vulnerability management and patching the systems that are most critical, exposed, and exploitable. You should also perform a gap analysis of your security controls aligned to your map of assets and compared with security best practices defined in any number of frameworks or regulations – then fill the big gaps first.
- Top-Level View: It is amazing how clear your security posture can be if you have the right level of visibility. If you are in the trees, focusing on the small rocks, it is hard to see the best path forward and planting more trees before you have a good view will only compound the problem. For cybersecurity effectiveness, organizations should first acquire good threat visibility through collecting enriched log and threat data. And then apply active monitoring and actionable alerting combined with orchestrated and automated threat response. This approach is called Managed Detection and Response. Understanding your high-level security posture and relative risk also requires continuous business intelligence for IT security. Ask your team or managed security services partner for a comprehensive dashboard providing this visibility.
- The Plan: Have a plan for success and work through your plan. Too often, we think that if we ignore the noise it will go away or we are caught in the trap of playing whack-a-mole for every compromise without figuring out how to keep the mole out of your yard. Success arrives when you tune your visibility to actionable threats, use your map, patch the right holes, and look at the forest from a high-level view. Only when the noise is reduced and vision focused, are you equipped to implement a comprehensive response plan. Such a plan will include detection of the threat, acknowledgment and triage of next steps, and containment and resolution of the immediate threat to your business. You must fully remediate the cause of the threat, so it does not reoccur. Lastly, your plan should include measuring your security posture and response lifecycle, and always be making improvements.
My recommendation to cybersecurity leaders is to write down your “big rock” objectives and list the key outcomes needed to accomplish them. Your teams will appreciate the clarity of vision and join in your mission to reach these goals on your combined journey.
For more detail on how we help executives achieve their cybersecurity objectives, please feel free to contact us at info@proficio.com.
By Brad Taylor | CEO | Proficio