OVERVIEW
Phishing events are commonly seen in the public so the Proficio’s threat intelligence team often receives opportunities to research different type of phishing activities. On the 13th November 2020, a client had requested for assistance on a phishing incidence that had occurred within their environment.
In this blog, we share some of the findings from our own deep-dive investigations into the HTM spear-phishing email campaigns.
PHISHING DETAILS
In this type of phishing attempt, the adversary would send a spear-phishing email with a HTM (.htm) file attach containing a URL link to the victim. Based on the team’s investigation of the incident that was reported, upon clicking on the phishing link it would redirect the victim to a phishing page which was hosted on another domain.
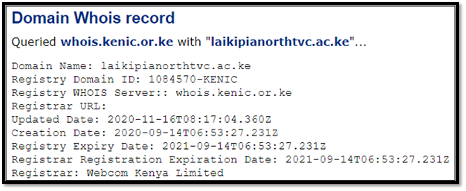
In this incidence, the phishing link was observed to be hosted on the domain “bayleafinternational[.]com” and upon clicking, the page would be redirected to the domain “laikipianorthtvc[.]ac[.]ke”. However, by 18th November 2020, the redirected phishing domain was taken down so instead of the first observed site “laikipianorthtvc[.]ac[.]ke”, it would redirect the user towards the domain “altia[.]in”. A Whois lookup (Figure 1) was performed on the first redirected link “laikipianorthtvc[.]ac[.]ke” and based on the updated date, it is suggested that this site was likely to taken down on 16th November 2020.
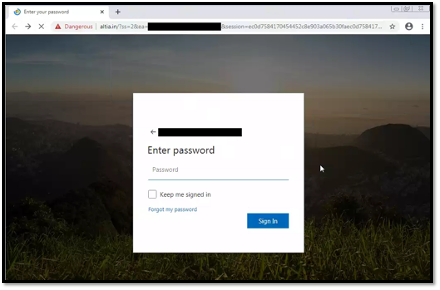
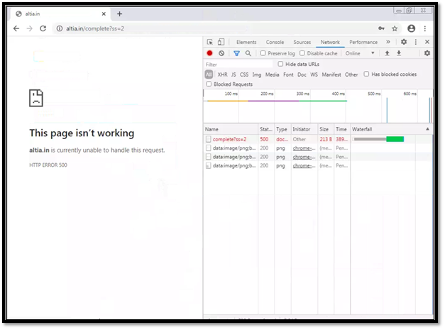
The team further investigated the redirected phishing link. Simulating access of the phishing domain would display a phishing page that resembles a Microsoft login page (Figure 2). Upon entering the credentials, we noticed that the phishing site would redirect the victim to a URL on the same domain with a URL path containing “/complete?ss=2”. In this incidence that we were investigating, the user was redirected to the request URL “hxxps://altia[.]in/complete?ss=2”. A HTTP POST request could also be identified upon submitting the credentials (Figure 3).
Similar phishing activities were also found in the wild, with our research suggesting that this phishing campaign appears to have started as far back as 1st September 2020; it is likely this phishing campaign is still ongoing. We have noticed that multiple domains were being used in this phishing campaign, but some of the used and older pages have since been taken down.
Comparing the phishing activities observed with those seen in the wild, aside from the same fake Microsoft login page used, the phishing links appears to share similar naming formats as follows:
- Initial URL from email
- <domain>/<base64-encoded victim’s email address>
- Redirected phishing page
- < phishing domain>/?ss=2&ea=<victim email address>&session=<session ID>
- Redirected complete page
- <phishing domain>/complete?ss=2
- <phishing domain>/complete?ss=2
MITRE ATT&CK FRAMEWORK
The following framework is produced based on the investigated incidence:
| Tactics | Techniques | Use |
| Reconnaissance [TA0043] | Phishing for Information: Spearphishing Link [T1598.003] | The phishing email contains a HTM file with a phishing link that leads to a fake login page used to steal credentials |
| Defense Evasion [TA0005] | Masquerading: Match legitimate name or location [T1036.005] | The phishing email contains the use of a htm files with the file name containing the client’s domain. |
| Initial access [TA0001] | Phishing: Spearphishing Link [T1566.002] | The adversaries utilize spear phishing emails and redirect victims to credential harvesting sites. |
PRECAUTIONARY MEASURES
Anyone can fall victim to a phishing attack. Cybercriminals offer try and catch unsuspecting individuals by sending a phishing email from a reputable or known users that they wouldn’t expect to be compromised. It is advisable to safeguard yourself and your organization to avoid being the next victim from phishing attacks and credential theft. We would recommend organization to consider the following measures if this has seen within your environment.
- Educate your employees and users to improve cybersecurity awareness.
- Remind users to report any suspicious emails received, even from other employees, to their cyber-security team.
- Apply content filters on email gateways and email systems to prevent malicious content from reaching users and reduce the chance of a possible compromise.
- Always verify any suspicious emails through a different channel such as calling the supposed sender for verification.
- If your organization is expecting legitimate emails from the senders, filter by email subjects and quarantine emails sent from those compromised senders to anyone outside of an expected recipient list.
- Reach out to any legitimate sender that appear have their account(s) compromised and instruct them to take action to secure their account(s).
- Make use of Multi-Factor Authentication to secure email and other user credentials.
- Make use of network segmentation alongside the zero-trust model.