Society has learned a lot of lessons in 2020. While many may focus on the covid-19 pandemic, it’s fair to say that cybersecurity faced its share of challenges too – especially with many organizations being thrust into a remote working environment.
For Proficio’s Threat Intelligence team, we had to face a slew of new threats, all while battling some familiar faces as well. We spent the last year doing extensive threat hunting campaigns, learning and improving along the way.
Here are three things we’ve learned this year and how you can use them to improve your cybersecurity in 2021.
1. Old Threats, New Faces: Malware and Phishing Continue to Endure
In 2020, malware, often in the form of a ransomware attack, continued to be incredibly prominent. The most popular variants we encountered were those that exfiltrated the victim’s data as a way of threatening victims who refuse to pay their ransom, such as REvil/Sodinokibi and DoppelPaymer.
Also popular are phishing attacks, which continue to be a key technique utilized by all classes of attackers. This was especially noticeable when many cybercriminals took advantage of COVID-19 as a topic to lure victims, but there have also been other varieties of phishing campaigns with different contents and formats to trick victims. As hackers adapt to a reality where cloud service offerings like Office 365 are increasingly used in corporate environments, one very common tactic we observed is the use of fake Microsoft login pages. We have been able to identify a significant number of these during our threat hunting campaigns.
There have also been multiple attack campaigns that utilized unpatched vulnerabilities in widely used software. Some examples of campaigns that we have investigated include attacks on the Citrix vulnerability (CVE-2019-19781) as well as the Zerologon vulnerability. There are also campaigns that exploit software updates instead of a vulnerability in the software, and compromise victims via the compromised updates. Some examples of this include the GoldenSpy campaign and the recent SolarWinds Sunburst campaign.
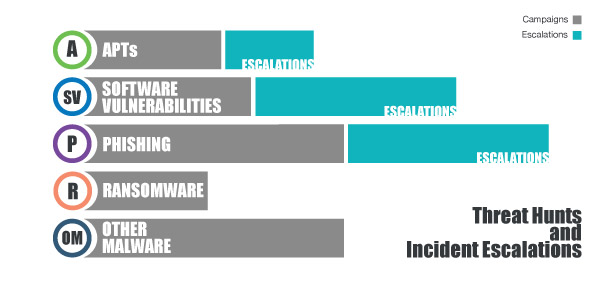
Below is the breakdown of threat hunting campaigns we have conducted throughout 2020. It also highlights where we had identified and escalated incidents of true positive hits to our clients.
While attackers will continue to use these avenues to exploit victims, there are still some common precautionary measures that can be taken to further safeguard you and your organization:
- Keep your anti-virus software / EDR solutions and other security tools installed on the systems updated for detection and prevention from the spread of ransomware.
- Performing regular backups on critical files and systems.
- Keeping your operating systems up to date on the latest security patches.
- Make use of network segmentation alongside the zero-trust model.
- Close unnecessary network ports to reduce entry points for attackers.
- Apply content filters on email gateways and email systems to prevent malicious content from reaching users and reduce the chance of a possible compromise.
- Educate your employees and users to improve cybersecurity awareness.
2. The Constant Evolution: Handling Increasingly Disparate Threats
Given the ever-evolving threat landscape, Proficio’s Threat Intelligence Team is constantly on the lookout for the newest cyber threats. We keep a close eye on the news and initiate threat hunting campaigns for threats are likely to have an impact on our clients. Throughout 2020, we conducted a significant number of threat hunting campaigns based on this research as well as threats found within our clients networks. We continually are looking for ways to improve how we conduct our threat hunting campaigns, as well as how we store and share information of interest with our internal teams and clients, to maximize our efficiency and make sure we give our clients the best protection possible.
When our team was first established, most threat hunting campaigns were self-contained within the Threat Intelligence team. As time progressed, and threats became increasingly complex, we found ourselves working with other internal teams, such as Security Advisors or Project Managers. We find collaborations can make us more effective and ensures all teams within Proficio are able to quickly and efficiently take appropriate actions when required, ensuring consistency of our security operations.
In addition, the structure and methodology we used for carrying out our threat hunting campaigns grew increasingly more robust throughout the year. We are better able to conduct rapid-response research and data collection efforts, with a clear plan of actions and priorities for every campaign we embark on. Depending on the extent of the hunt and the platforms used for searches, the amount of time taken to provide our clients with our investigation findings can vary from a few days to over a week; However, these efficiencies and improved methodology have allowed us to decrease our turnaround time.
In order to adapt to the more complex threat landscape, our threat hunting campaigns must continue to evolve; we have gone from using simple IOCs, like file hashes and IP addresses, to tactics, techniques and procedures tied to that of our adversaries. We have also transformed the way we document our threat hunts. We found that by enhancing our investigation write-ups with threat diagrams, attack maps and incorporating the MITRE ATT&CK classification framework, we are better able to organize our findings to create a library. We also take inspiration from documentation produced by other well-established security organizations sharing information such as JPCERT.
Creating a library of your threat hunts over time is a great way for any organization to better track the adversaries your organization is dealing with. In addition, the cybersecurity community has a tremendous amount of open source tools to take advantage of, that will better help us all defend against cybercriminals.
3. Outside Looking In: Synergizing Efforts to Create Maximum Value
As a team, we are always looking for ways to synergize everything we do as force multipliers that help make a big impact on all our clients.
We keep up with threat news and developments in cybersecurity on a daily basis, sharing those that we found to be potentially relevant on our official Twitter account. We also have a Threat Intelligence page, where you can sign up to receive a weekly threat digest with the top threat news each week.
These tools play a big part in our ongoing data collection efforts, allowing us to better track trends in cyberattacks across different industry sectors as well as document known threat group activities. The data collected also plays a big role in terms of our decision to initiate threat hunting campaigns, with the goal of identifying potential attacks or existing compromises that might have slipped past the cracks.
One of the greatest things about the cybersecurity community is that they are open to sharing knowledge in our joint efforts to combat cybercriminals. We recommend you join communities and follow along with the latest trends – and if you’ve found something, we encourage you to also share what you learned, so others can benefit from your research! That’s how we make the community stronger, one threat hunting campaign at a time.
While the Threat Intelligence team observed numerous new cyberthreats throughout 2020, we have no doubt the uphill battle on cybercrime will continue into 2021 and beyond. We will continue to conduct high-quality investigations for our clients for any relevant threats and share these findings, both with our clients and the community as a whole, in hopes to do our part in this war on cybercrime.