A global effort must be made to help ensure everyone stays safe and protected when using technology whenever and however you connect. As Cybersecurity Awareness Month comes to a close, we want to leave you with a recap of what social engineering is, how the threat actors operate and how to spot a social engineering attack.
Proficio is spotlighting four fundamental cybersecurity behaviors. Each of these behaviors is vital for safeguarding your digital life. We want to highlight the “Secure Our World” initiative from CISA (Cybersecurity and Infrastructure Security Agency). It is a year-round effort that aims to promote cybersecurity best practices and tips for individuals and businesses. Here are the key takeaways you can apply and encourage others to follow for phishing and other cyber threat prevention.
Phishing and Cyber Threat Prevention
1. Create Strong Passwords and Use a Password Manager:
Creating strong passwords and managing them securely is the first line of defense against cyber threats. Weak passwords are easy targets for hackers.
By using complex, unique passwords for each of your accounts (made easier by employing a password manager), you significantly reduce the risk of unauthorized access. Strong passwords act as a robust barrier, protecting your sensitive information and digital identity.
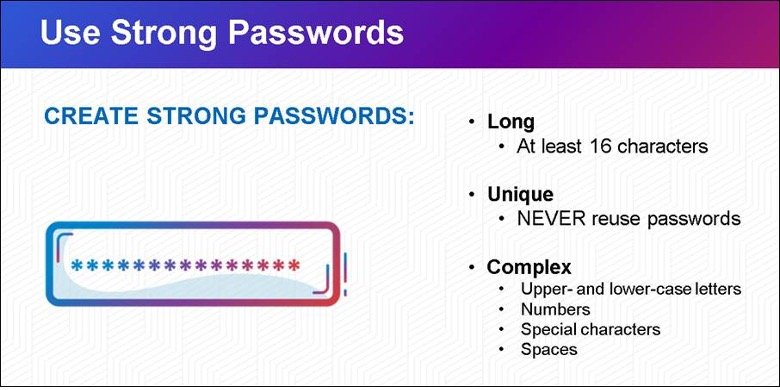
Source: https://www.cisa.gov/
2. Turn On Multifactor Authentication
Multifactor authentication (MFA) adds an extra layer of security by requiring users to verify their identity through multiple methods, such as passwords, biometrics, or security tokens.
Enabling MFA ensures that even if your password is compromised, unauthorized access is thwarted. It is a powerful tool in safeguarding your accounts and maintaining the confidentiality of your data.
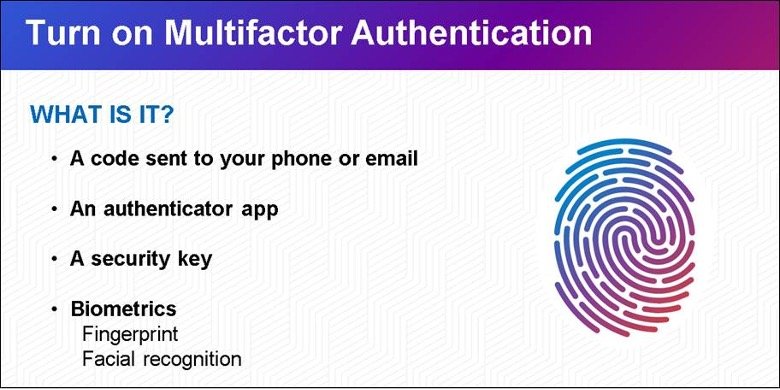
3. How to Recognize and Report Phishing
Phishing attacks continue to be a prevalent threat in the digital landscape. Cybercriminals use deceptive emails, messages, or websites to trick individuals into revealing sensitive information.
Recognizing phishing attempts and reporting them promptly is essential. By staying vigilant and educating others, you contribute to creating a safer online environment. Reporting phishing incidents enables your IT team and authorities to act, preventing further scams and protecting potential victims.

4.Update Your Software
Regularly update your software, including operating systems, browsers, and applications.
Software updates often include security patches that address vulnerabilities exploited by cyber attackers. Failing to update your software leaves your devices and data exposed to potential exploits.
By staying current with software updates, you ensure that your systems are equipped with the latest security features, enhancing overall protection against cyber threats.

We encourage you to embrace these cybersecurity behaviors as part of your daily digital habits. By incorporating these practices into your routine, you play an active role in securing our digital world.
Join us in spreading the word about “Secure Our World” and let’s work together to create a safer online environment for everyone.
Social Engineering – The Art of Deception
Social Engineering is a common strategy in phishing attacks. Threat actors manipulate their targets into breaking normal security procedures or divulging confidential information.
One of the most common social engineering trends we have observed this year was attackers pretending to be executive staff, tricking users into providing sensitive data. Being able to identify the characteristics of these attempts is vital to maintain a strong security posture.
The Psychology of Social Engineering
Attackers often claim to be internal leadership or a trusted authority figure in an organization for several reasons:
- Authority: People are more likely to follow instructions or requests that come from a person of authority. By impersonating these figures, attackers can exploit the psychological tendency to increase the chances of their phishing attempts being successful.
- Urgency: Messages from leadership often carry a sense of urgency or importance, making the recipient more likely to act quickly without thoroughly verifying the request or authenticity of the email.
- Trust: Employees generally trust communications from their superiors and colleagues. Attackers exploit this trust to trick employees into revealing sensitive information, clicking on malicious links, or even transferring funds.
- Fear of Consequences: Employees may fear negative consequences if they ignore or question a request from a high-level executive. This fear can push them to comply without due diligence.
- Lower Suspicion: Emails from internal sources or well-known contacts are less likely to be marked as spam or to raise suspicion.
Types of Phishing Attacks
Add a new one to the list – Quishing!
- Quishing: QR code phishing, now known as Quishing, involves deceiving someone into scanning a QR code using their mobile device. The QR code then leads the user to a fraudulent website that might download malware or ask for sensitive information.
- Spear Phishing: A Spear Phishing attack is a phishing attempt crafted to trick a specific person rather than a wider target. The attackers research the target, or they aim to gather that information to advance their objectives. Once personal details are obtained, such as a birthday, the phishing attempt is tailored to incorporate that personal detail(s) to appear more legitimate. These attacks are typically more successful because they are more believable. In other words, this type of attack has much more context (as outlined by the NIST Phish Scale) that is relevant to the target.
- Whaling: Whaling is a sub-type of Spear Phishing and is typically even more targeted to specific high-value individuals such as business executives, celebrities, and people with high-net-worth. Access to their account credentials typically provides a gateway to more information and financial gain.
- Smishing: Smishing is a type of phishing attack deployed via SMS message. This type of phishing attack gets more visibility because of the individual’s notification and because more people are likely to read a text message than an email. Smishing attempts have escalated with the rising popularity of SMS messaging between consumers and businesses. If you receive a text message asking you to send personal information or money, do not reply. Replying to the message lets the attacker know it is an active number and an attack will continue.
- Vishing: Vishing is a type of attack carried out via phone call. The attackers call the victim, usually with a pre-recorded message or a script. In a recent X (formerly Twitter) breach, a group of hackers pretending to be “IT Staff” were able to convince Twitter employees to hand over credentials all through phone conversations.
Why Use of QR Codes in Phishing Campaigns is Increasing
Because it is easy to generate QR codes using free online tools, QR codes are a simple and scalable attack vector. Attackers place a fake QR code sticker over a legitimate QR code posted to public websites. That fraudulent QR code can lead unknowing users to phishing sites that mimic legitimate websites. Attackers employ QR code spoofing in social engineering tactics more and more. Enticing offers and urgent emails motivate the user to scan the code. How attackers leverage QR code spoofing to achieve their end goal:
- Malware Distribution: QR codes can be linked to websites malicious websites. For example, when a user scans the QR code, they could be redirected to a website that automatically downloads malicious software onto their devices, opening the door to unauthorized access or data theft.
- Fake App Downloads: Scanning a QR code in an email might prompt users to download a malicious app, disguised as a legitimate one. Once installed, the app could compromise the user’s device, infect it with malware, malicious pop – up ads or more.
- Credential Harvesting: Attackers can craft QR codes that lead to phishing sites posing as log in pages. Unsuspecting users may scan the QR code and enter their user id and passwords, thinking they are logging into a legitimate service. The attackers then harvest credentials and put them up for sale on the dark web marketplace or use them for personal or financial gain.
- Tech Support Scams: Scammers can use QR codes to redirect users to fraudulent tech support websites or phone numbers. Users might fall for calling the provided number, where scammers pose as tech support agents, tricking victims into handing over their credit card information or gaining remote access to their devices.
Real Life Examples Phishing Emails Sent to Proficio Executives
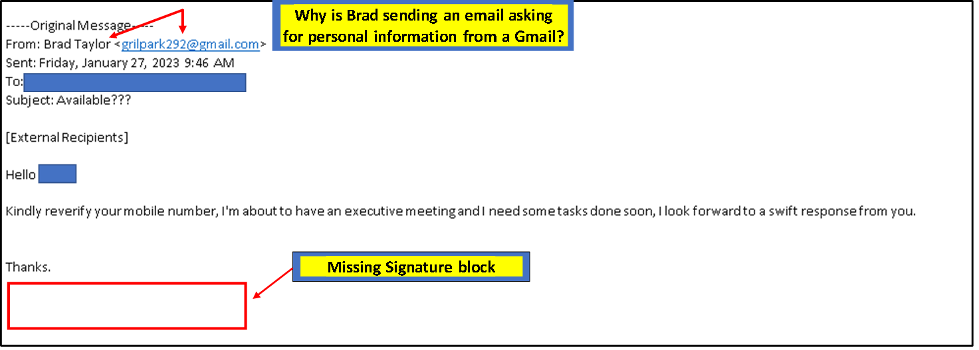
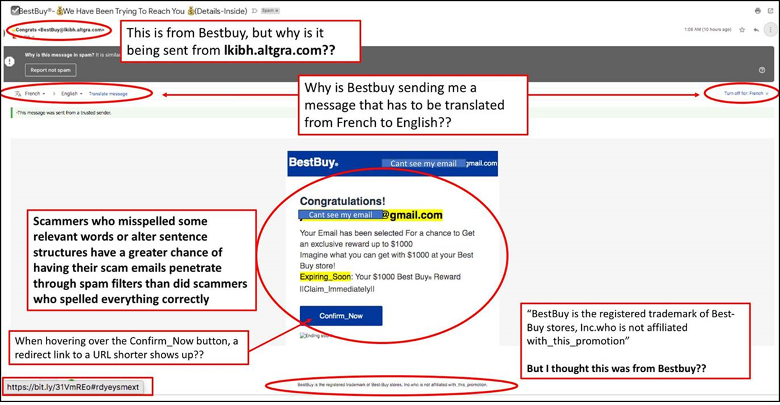
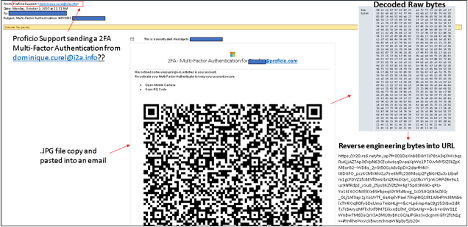
When using QR Codes, follow these steps first:
- Double check the URL that pops up before proceeding to a site – especially if you are asked to enter any information. Does it look suspicious?
- Use a QR scanning app that checks for malicious links.
- Avoid scanning QR codes from unknown sources.
- Monitor accounts after scanning for unauthorized activity.
If you receive an email that appears suspicious, make sure to verify the contents by calling the sender, using an internal messaging system or any other medium. Make sure to notify your IT department.
Don’t Forget – Social Engineering Red Flags
1. Grammar and Spelling Errors
One of the more common signs of a phishing email is bad spelling and incorrect grammar. Most businesses have the spell check feature on their email client turned on for outbound emails. Applying autocorrect or highlighting features on most web browsers is also possible. Therefore, emails from a professional source should be free of grammar and spelling errors.
2. Inconsistencies in Email Addresses, Links & Domain Names
Look for discrepancies in email addresses, links, and domain names. If you suspect phishing, check that the email address matches the sender’s email. Hover the cursor over any embedded links to verify URLs behind hyperlinked text are legitimate. If the email is allegedly from PayPal, but the link’s domain does not include “paypal.com,” that’s a huge giveaway. If the domain names don’t match, don’t click.
3. Threats or a Sense of Urgency
Another tactic attackers use is creating a sense of urgency to fluster the recipient. Emails that threaten negative consequences should always be treated with suspicion. The attacker hopes that if their target reads the phishing email in haste the hallmarks of a phishing campaign might not be detected.
4. Suspicious Attachments
If an email with an attached file is sent from an unfamiliar source, or if the recipient did not request or expect to receive a file from the email’s sender, the attachment should be opened with caution. If the attached file has an extension commonly associated with malware downloads (.pdf, .zip, .exe, .scr,.html, etc.) – or has an unfamiliar extension – recipients should flag the file to be virus-scanned before opening.
5. Unusual Request
If an email sender has an unusual request, that can also indicate that the message is potentially malicious. For example, if an email claims to be from the IT team asking the recipient to perform tasks typically handled by IT, that’s a big clue that you have received a phishing email, should not follow the instructions, and report it to IT.
6. Request for Credentials, Payment Information or Other Personal Details
One of the most sophisticated phishing emails is when a recipient is directed to a fake landing page via an email link and prompted to log in. Recipients should check out the website from which the email was supposedly sent by typing in the URL – rather than clicking on the link in the email – before entering their login credentials into the fake site or making a payment to the attacker.
At Proficio, we use phishing attempts to identify behavioral trends with specific users, understand the social engineering methods being used in the emails, and to detect any malicious content being sent to our users. It’s important to remember regardless of the sender, always 1. verify, 2. validate, and 3. confirm that an email is legitimate before replying or clicking on any links or scanning a QR code. And, trust your gut. If the email looks suspicious, it probably is. Learn more about Proficio and how we can help you.
Phishing and Cyber Threat Prevention are paramount in today’s always online culture. There are constant threats and new tactics developed every day. Follow our blog for more updates and news about cyber security and prevention.