OVERVIEW
Ryuk ransomware was first discovered in the wild in 2018. It is known for using manual hacking techniques and open-source tools to move laterally through private networks and gain administrative access to as many systems as possible before initiating the file encryption.
This ransomware group was one that did not stop attacks on healthcare organizations despite the Coronavirus pandemic in 2020, made clear by their recent attack against Universal Health Services (UHS). In this blog, we will share the common IOCs for this type of attack and ways to stay protected.
RANSOMWARE DETAILS
Since 2019, the most common method for Ryuk threat actors to gain entry to a victim’s environment is with the use of Trickbot and Emotet malware, often starting with phishing attacks. In the case of the UHS attack, both Emotet and TrickBot were detected within the UHS’ environment.
The attack chain often starts with delivering Emotet to a victim host via phishing email, which subsequently downloads Trickbot onto the host. After harvesting data, Trickbot opens a reverse shell to provide Ryuk ransomware threat actors with entry to the victim’s environment, allowing the actors to manually deploy the ransomware on the victim host.
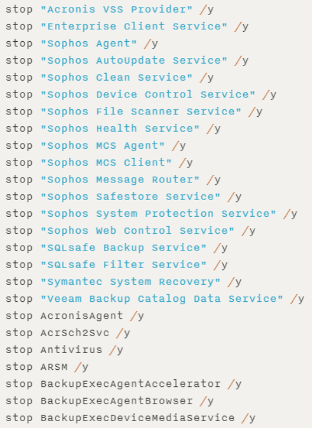
Ryuk ransomware has been found to contain commands for killing services related to antivirus products, and Trickbot has the capability to disable Microsoft Defender as well. A UHS employee has stated online that during the attack, “multiple antivirus programs were disabled”.
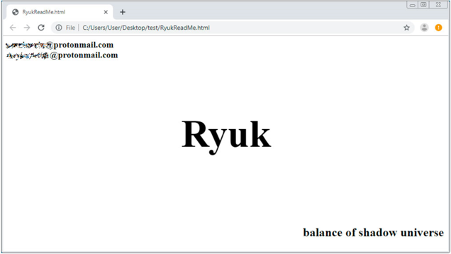
According another UHS employee, one of the infected computers displayed a ransom note that read “Shadow of the Universe”, which is similar to the phrase “balance of shadow universe” seen in previous Ryuk ransom notes. Names of files were observed being appended with the file extension “.ryk”, which is the extension used by Ryuk ransomware after successfully encrypting a file.
While there are limited details on the UHS attack, there are some common activities and IOCs of Ryuk ransomware attacks involving Trickbot and Emotet:
- Phishing email containing Microsoft Office attachments (.doc, .xls etc.) with Macros
- PowerShell commands executed by Macros
- Downloading of PowerShell Empire/Cobalt Strike/PsExec
- Exploitation of EternalBlue vulnerability which is over port 445 (SMB)
- Unusual scheduled tasks, registry keys created
- Recurring traffic towards Trickbot C2 servers over ports such as ports 446, 447, 449, 8082
- Privilege escalation
- Files with the file extension “.ryk”
- “RyukReadMe.txt” or “RyukReadMe.html”
PRECAUTIONARY MEASURES
Prevention is better than cure. It is advisable to safeguard yourself and your organization to avoid being the next victim of this ransomware attacks. We would recommend the following measures:
- Keep your anti-virus software / EDR solutions and other security tools installed on the systems updated for detection and prevention from the spread of ransomware
- Consider Managed EDR services that will enable you to quickly react and contain any ransomware vendor
- These services can also play a big part in monitoring and alerting on attacked vectors used as a distribution method
- Have a cold or distributed backup system in place
- At a minimum, have backups separate from production systems for your critical files or systems
- Keep your operating systems up to date on the latest security patches
- Make use of network segmentation alongside the zero-trust model
- Close unnecessary network ports to reduce entry points for attackers
- Apply content filters on email gateways and email systems to prevent malicious content from reaching users and reduce the chance of a possible compromise
- Educate your employees and users to improve cybersecurity awareness
REFERENCES
- https://www.bleepingcomputer.com/news/security/uhs-hospitals-hit-by-reported-country-wide-ryuk-ransomware-attack/
- https://techcrunch.com/2020/09/28/universal-health-services-ransomware/
- https://www.crowdstrike.com/blog/big-game-hunting-with-ryuk-another-lucrative-targeted-ransomware/
- https://research.checkpoint.com/2018/ryuk-ransomware-targeted-campaign-break/
- https://www.cybereason.com/blog/triple-threat-emotet-deploys-trickbot-to-steal-data-spread-ryuk-ransomware
- https://www.bleepingcomputer.com/news/security/new-trickbot-version-focuses-on-microsofts-windows-defender/
- https://www.microsoft.com/security/blog/2020/03/05/human-operated-ransomware-attacks-a-preventable-disaster/
- https://www.cpomagazine.com/cyber-security/ryuk-ransomware-still-targeting-hospitals-during-the-coronavirus-pandemic/
- https://www.bleepingcomputer.com/news/security/ryuk-ransomware-keeps-targeting-hospitals-during-the-pandemic/
- https://www.bleepingcomputer.com/news/security/ryuk-ransomware-attacked-epiq-global-via-trickbot-infection/