 For the past twelve years, Microsoft’s Patch Tuesday has been a monthly reminder of the challenges with vulnerability remediation. For IT and security teams, Patch Tuesday means it’s time to assess another batch of security updates and decide which ones to deploy and when, and which ones to either defer, indefinitely or at least temporarily. Microsoft’s steady stream of updates, combined with those from other enterprise vendors, is enough to keep IT teams very busy. And then there’s the periodic “BIG ONE’s” such as Heartbleed, Shellshock, or Poodle that have widespread impact (more work) and invite intensive executive-level interest (more oversight) in the vulnerability remediation process.
For the past twelve years, Microsoft’s Patch Tuesday has been a monthly reminder of the challenges with vulnerability remediation. For IT and security teams, Patch Tuesday means it’s time to assess another batch of security updates and decide which ones to deploy and when, and which ones to either defer, indefinitely or at least temporarily. Microsoft’s steady stream of updates, combined with those from other enterprise vendors, is enough to keep IT teams very busy. And then there’s the periodic “BIG ONE’s” such as Heartbleed, Shellshock, or Poodle that have widespread impact (more work) and invite intensive executive-level interest (more oversight) in the vulnerability remediation process.
As quickly as IT and security operators familiarize themselves with new vulnerabilities and updates, so do cybercriminals— as means of creating, trading, or renting exploits. And with profit as motivation, cybercriminals are at least as attentive as IT staffs, if not more so. While these bad actors have access to easily deployed exploits and can choose their targets, every organization is facing tighter budgets and a growing numbers of devices and applications. In this cyberwar, the cybercriminals are better equipped for their mission than the defenders inside the organization.
While very informative, the details accompanying vulnerability scans can also be overwhelming for many organizations. The IT staff may have plenty of data on vulnerabilities and on the remediation alternatives for them, but there’s so much information it’s difficult for many IT staffers to know where to begin. Do you start with:
- High severity vulnerabilities?
- Vulnerabilities that affect the key run-the-business systems?
- Vulnerabilities that are getting the most attention in the form of exploits?
What’s Important?
The answer isn’t that simple. Your priority is not to remediate every vulnerability. It’s to manage the risk posed by the vulnerabilities, which means knowing which assets in your infrastructure are most valuable to the business. With the perspective of asset value, you can then focus on which vulnerabilities to assess. In most organizations, the analysis process is manual. This requires people to be knowledgeable about how their networks, servers and applications are configured.
Next….
Once you know which vulnerabilities matter, you still have to decide what to do. For example
- Some vulnerabilities are effectively non-exploitable — the host systems or applications are sufficiently protected with compensating controls that the chances of an exploit being successful is close to zero.
- Some vulnerabilities are resident because the application or server includes older versions of software —if upgraded, this will break the application or service.
- Some vulnerabilities impact systems or applications that are so critical to running the business that you cannot risk any action that could disrupt the system or application
Adding It All Up: It’s Time-Consuming
Working through all of the above analysis just to get to a point where you actually perform the remediation takes a lot of time. Time you probably need to devote to other activities. Time you definitely can’t make up. NopSec recently released the results of study, (below) which we’ve excerpted a table. . The key take-away — many organizations take a lot of time to remediate vulnerabilities; 176 days in the case of Financial firms. That’s a really long window of exposure for any organization!
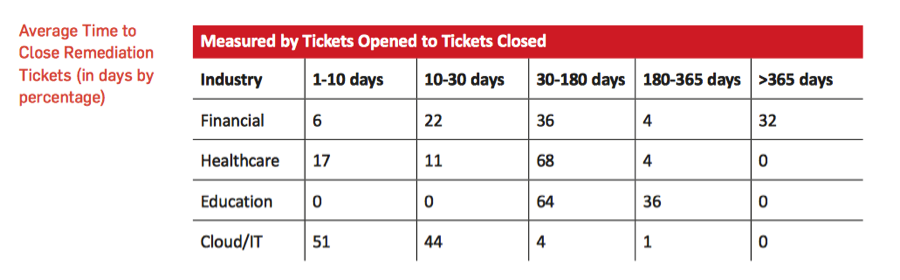
We’ve heard about this problem from a lot of companies we talk to and we know the effort that’s required in our own operations to address vulnerabilities. That’s why we created a service to address this problem for our customers. Please check it out and let us know if you think we’re on target – or off. Oh – and Patch Tuesday…? Microsoft has been less than clear on whether this will continue or morph to something less regular. Let’s hope for us all that they will continue to help us keep the important information safe.