Imagine how much damage a hacker could do by compromising your Active Directory.
Active Directory, which is used by an estimated 95% of Fortune 5000 companies, forms the core services for security and permissions management. It allows IT administrators to configure permissions through one console to ensure their users and computers align with their company’s policies.
Through a single sign-on operation performed by users, Active Directory provides users with access to many of the available network resources, including emails, computers, shared files and folders, applications, and more.
Active Directory also enables IT administrators to lock down security policies for certain groups of users, computers, and applications such as limiting what files shared computers in a laboratory can access, disabling access to the Control Panel, and preventing access to USB drives.
These powerful capabilities of Active Directory, coupled with its widespread adoption, make it a primary target for hackers. Often, cyber attacks aim at escalating privileges or compromising an administrator account to gain unauthorized access – which could make you vulnerable to a major data breach. In fact, several of the key steps taken in recent attacks on large retailers involved exploiting Active Directory.
So what is Proficio doing differently to help customers prevent attacks on Active Directory?
Correlation Rules for Indicators of Compromise
First, we created correlation rules inside our SIEM for the events classified by Microsoft as potential indicators of compromise for Active Directory. These rules flag suspicious behavior rated with high potential criticality that should be investigated.
Examples of events with high potential criticality are as follows*:
| Windows Event ID | Potential Criticality | Event Summary |
|---|---|---|
| 4618 | High | A monitored security event pattern has occurred. |
| 4649 | High | A replay attack was detected. |
| 4719 | High | System audit policy was changed. |
| 4765 | High | SID History was added to an account. |
| 4766 | High | An attempt to add SID History to an account failed. |
| 4794 | High | An attempt was made to set the Directory Services Restore Mode. |
| 4897 | High | Role separation enabled. |
| 4964 | High | Special groups have been assigned to a new logon. |
| 5124 | High | A security setting was updated on the OCSP Responder Service. |
*Reference: Microsoft Active Directory Events to Monitor
Let’s examine Event 4719, a change in the system audit policy, as an example. Under normal conditions, the system audit policy is never changed by users. Audit policy changes are typically only done by a top-level Active Directory administrator. The system audit policy could have a rule to create a log when an account fails to logon for 3 times in a row. If a hacker is able to change the system audit policy without being detected, they give themselves an opportunity to brute force logon. Therefore it is important for the SIEM to monitor for Event 4719.
Correlation Rules for Suspicious Activities
Second, we created correlation rules for a large number of other suspicious events that have to do with group changes, accounts lockouts, failed logons, and other operations. Let’s take a closer look at these:
Group Changes
For group changes, Active Directory has sensitive default groups that should be monitored. Proficio ProSOC monitors these groups for changes to detect suspicious activity. Proficio also has the ability to monitor custom groups and look for added or removed users from groups of interest. For further information on default groups available in Active Directory please refer to the following article.
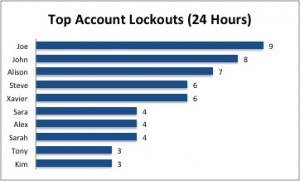
Account lockouts
For account lockouts, our solution can be customized for both a small organizations as well as large organizations.
For smaller organizations, Proficio provides real-time alerting on each individual account lockout. Setting up correlation rules around this event in small environments can provide valuable insight to the organization.
For larger organizations, reviewing every account lockout in real-time is not feasible. Therefore correlation includes filtering down account lockouts to privileged accounts in a certain group or accounts that have a special business function within the organization. The reasoning behind this is to detect a locked out account that performs services or tasks that could have a serious impact on the organization when an account lockout occurs.
Failed Logons
It can be easy for administrators to get overwhelmed by the amount of failed logons, particularly when the system has a large number of users.
Selecting specific failed logons of interest for reporting or correlation is key for strong used cases around failed Active Directory authentication. For example, interactive and remote interactive failed logons are usually more notable than failed network logons.
Proficio designs specific use cases to fit our customers needs during the onboarding process. One example is alerting on failed remote interactive logons for privileged user accounts. We also track suspicious OWA failed authentication activity.
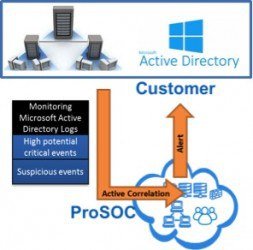
Detection and Alerting in Real-Time
After the log events are collected from the customer network and sent in an encrypted channel to our Security Operations Centers (SOC), certified security analysts continuously monitor them on a 24x7x365 basis. Once an event is detected about an Indicator of Compromise or the other suspicious activity discussed in the previous section, it is investigated by trained SOC analysts.
In cases where the analysts determine that the threat is real or that a compromise has occurred, we immediately alert the customer. The alerting mechanism is customizable and is agreed upon during the customer on-boarding process.
Graphical Dashboards and Reporting
We also provide additional tools for our customers to visualize potential anomalies to policy or unauthorized activity; these come through our ProView SIEM portal by use of graphical dashboards, policy and configuration change reports, and log search investigative analytics.
Because Proficio runs cloud-based security services, a Windows Administrator is able to take a quick view of a dashboard and visualize abnormal or unauthorized activity that may not otherwise be discovered. Change management reports are provided to determine who made specific changes.
Below is an example of a chart available for customers: