Overview | Darkside Ransomware
DarkSide ransomware was first discovered in the wild in August 2020. It runs a Ransomware-as-a-Service (RaaS), whereby affiliates are able to deploy the ransomware for a fee or a cut of the proceeds from successful ransom payments.
The DarkSide ransomware group was brought to mainstream attention due to the recent ransomware attack against Colonial Pipeline. The Proficio Threat Intelligence Team posted information and articles about the Colonial Pipeline attack in our X Feed. Below, we provide more detailed findings based on our research of DarkSide ransomware.
What We Know About the DarkSide Ransomware Group
DarkSide ransomware group attacks are highly targeted, and affiliates are able customize the ransomware executable for the specific organization they are attacking. Organizations that are targeted typically have the finances to pay large ransom amounts. After the attack on Colonial Pipeline, the DarkSide ransomware group has publicly stated that they are apolitical and their goal “is to make money, not create problems for society”.
However, affiliates are not allowed to attack organizations from the following sectors:
- Healthcare
- Funeral services
- Education
- Public sector
- Non-profit organizations
- Government sector
The DarkSide ransomware group also has a website where they publish data stolen from victims who refuse to pay the ransom. This is a method of further pressuring victims to pay, following a trend observed among ransomwares throughout 2020, including DoppelPaymer and REvil/Sodinokibi.
How DarkSide Ransomware Attacks Work
The initial entry method of DarkSide ransomware attacks can vary depending on the affiliate carrying out the attack. There is currently no public information on the initial entry method used in the attack on Colonial Pipeline, however example methods observed from past DarkSide ransomware attacks include:
- Exploiting hardware/software vulnerabilities
- Exploiting remote access services (such as RDP)
- Access victim’s network using legitimate credentials, obtained by:
- Phishing attacks
- Password attacks (such as password spraying)
- Purchasing from a third-party source
After gaining access to the victim’s environment, the attackers will move laterally throughout the network and perform internal reconnaissance to gather information before encrypting data. The following have been observed being utilized in previous attacks for reconnaissance/lateral movement:
- PSExec
- RDP connections
- SSH
- Mimikatz
- Cobalt Strike
- BloodHound
Information gathered during the internal reconnaissance also includes credentials stored in files, memory and domain controllers; the stolen credentials are then used to access privileged accounts. PowerShell commands are executed to delete shadow copies which wipes backups and file snapshots to prevent recovery.
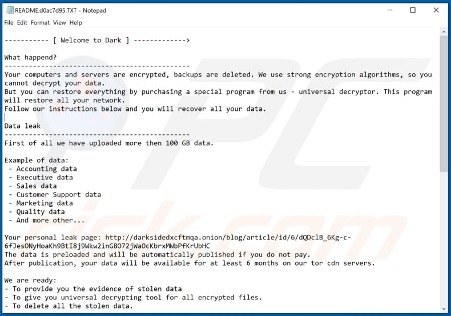
Stolen data is exfiltrated before deploying DarkSide ransomware to encrypt the victim’s files. Upon successful encryption, the ransomware appends a victim’s ID as an extension to file names. A ransom note with the naming convention of “README.[victim’s_ID].TXT” is dropped onto the victim’s device with instructions for the victim to access a Tor website using a Tor browser to pay the ransom – and if unpaid, they threaten to publish the stolen data.
Known DarkSide Affiliates
As previously mentioned, DarkSide ransomware can be used by different affiliates and as such, different Darkside attacks can utilize different tools and tactics depending on the affiliate. Below are examples of different attack flows by three affiliates that were identified by FireEye.
UNC2628
This affiliate group is suspected to have used a password spraying attack against the victim’s VPN to gain initial access into the environment. The attackers utilized Cobalt Strike beacons for C2 communications and Mimikatz for credential theft. Lateral movement was performed using RDP connections and Cobalt Strike.
The attackers exfiltrated stolen data using Rclone, a command line utility to manage files for cloud storage applications, to cloud-based storages. DarkSide ransomware is then deployed using PsExec.
The following is a MITRE ATT&CK table of this affiliate’s attack:
| Tactics | Techniques |
| Credential Access [TA0006] | Brute Force: Password Spraying [T1110.003] |
| Initial Access [TA0001] | Valid Accounts [T1078] |
| Resource Development [TA0042] | Obtain Capabilities: Tool [T1588.002] |
| Credential Access [TA0006] | OS Credential Dumping [T1003] |
| Lateral Movement [TA0008] | Remote Services: Remote Desktop Protocol [T1021.001] |
| Command and Control [TA0011] | Application Layer Protocol: Web Protocols [T1071.001] |
| Execution [TA0002] | Command and Scripting Interpreter [T1059] |
| Execution [TA0002] | System Services: Service Execution [T1569.002] |
| Exfiltration [TA0010] | Exfiltration Over Web Service: Exfiltration to Cloud Storage [T1567.002] |
| Impact [TA0040] | Data Encrypted for Impact [T1486] |
UNC2659
This affiliate group gains initial access by exploiting the SonicWall vulnerability CVE-2021-20016. After gaining access to the victim’s environment, the attackers download the tool TeamViewer from the official website onto the victim host to establish persistence within the environment.
This group was also observed utilizing Rclone for data exfiltration, which is downloaded from the official website onto the victim host. The stolen data is exfiltrated to cloud-based storages.
The following is a MITRE ATT&CK table of this affiliate’s attack:
| Tactics | Techniques |
| Initial Access [TA0001] | Exploit Public-Facing Application |
| Resource Development [TA0042] | Obtain Capabilities: Tool [T1588.002] |
| Command And Control [TA0011] | Remote Access Software [T1219] |
| Execution [TA0002] | Command and Scripting Interpreter [T1059] |
| Exfiltration [TA0010] | Exfiltration Over Web Service: Exfiltration to Cloud Storage [T1567.002] |
| Impact [TA0040] | Data Encrypted for Impact [T1486] |
UNC2465
This affiliate group utilized a backdoor named “SMOKEDHAM” to gain access to the victim’s environment, which is delivered via phishing emails and legitimate services such as Google Drive and Dropbox. Advanced IP Scanner, BloodHound, and RDP were used for internal reconnaissance, and Mimikatz was used for credential theft.
The attackers also used the NGROK utility to bypass firewalls and expose remote service ports such as RDP to the Internet. The DarkSide ransomware is deployed using PsExec and scheduled tasks.
The following is a MITRE ATT&CK table of this affiliate’s attack:
| Tactics | Techniques |
| Initial Access [TA0001] | Phishing: Spearphishing Link [T1566.002] |
| Resource Development [TA0042] | Obtain Capabilities: Tool [T1588.002] |
| Lateral Movement [TA0008] | Remote Services: Remote Desktop Protocol [T1021.001] |
| Credential Access [TA0006] | OS Credential Dumping [T1003] |
| Defense Evasion | Impair Defenses [T1562] |
| Execution [TA0002] | System Services: Service Execution [T1569.002] |
| Impact [TA0040] | Data Encrypted for Impact [T1486] |
General Recommendations
Although DarkSide ransomware attacks can involve different tactics and tools, based on which threat group is making use of their RaaS, the tactics, techniques and tools deployed are not completely different as they share the common DarkSide platform. The variety of tactics and techniques deployed should serve as a clear indication that focusing on any single threat will not provide adequate coverage, in terms of ensuring that an organization is well protected from the broad array of security threats.
The use of EDR solutions provide valuable visibility into endpoints and important systems, so they should play a big role in dealing with ransomware attacks. We also recommend a defense-in-depth approach for securing your network and environment, including ensuring there is proper segmentation and security device visibility between network segments, particularly critical network segments. Traditional security architecture, that focuses solely on securing the perimeter, are inadequate in dealing with modern day persistent threats, though they play an important part.
An organization with proper network segmentation and security device coverage can then make use of the following general suspicious indicators/activities that serve as a useful way to monitor for to identify potential DarkSide ransomware attacks:
- Attacks on VPN infrastructure (exploiting vulnerabilities or through password spraying attacks)
- Phishing emails
- Deployment, use and download of common exploit and bypass tools like Mimikatz, Cobalt Strike and BloodHound
- Unauthorized deployment, use and download of remote access tools (Teamviewer, Remote Desktop, etc)
- Installation of suspicious or unknown services
- Data exfiltration to cloud storage
Proficio has already deployed a wide variety of use cases that can be effectively utilized to detect such common indicators or activities. Of course, the effectiveness of the use cases depends on the log sources being monitored and their visibility into the environment or network. We recommend reaching out to your security advisors or client success managers to understand the use cases deployed for your environment and how we can work together to increase the efficacy of our monitoring, detection and discovery efforts.
The Proficio Threat Intelligence Team will continue to research and investigate all new threats to identify the best way to start a threat hunting campaign. And as always, we will keep all of our clients informed on our efforts in this area.
Precautionary Measures
Prevention is better than cure. It is advisable to safeguard you and your organization to avoid being the next victim of this ransomware attacks. We would recommend organization to consider the following measures.
- Keep your anti-virus software / EDR solutions and other security tools installed on the systems updated for detection and prevention from the spread of ransomware.
- Performing regular backups on critical files and systems.
- Keeping your operating systems and accessible services up to date on the latest security patches.
- Make use of Multi-Factor Authentication to govern access as much as possible.
- Make use of network segmentation alongside the zero-trust model.
- Close unnecessary network ports to reduce entry points for attackers.
- Apply content filters on email gateways and email systems to prevent malicious content from reaching users and reduce the chance of a possible compromise.
- Educate your employees and users to improve cybersecurity awareness.