Overview | Kaseya VSA
On July 2, 2021, right before Americans started their long, Independence Day weekend, hackers once again made their way to the top of the news headlines. This time, the victim of the largest ransomware attack was Kaseya, a technology company that sells its technology to other third-party providers, mainly managed service providers (MSPs).
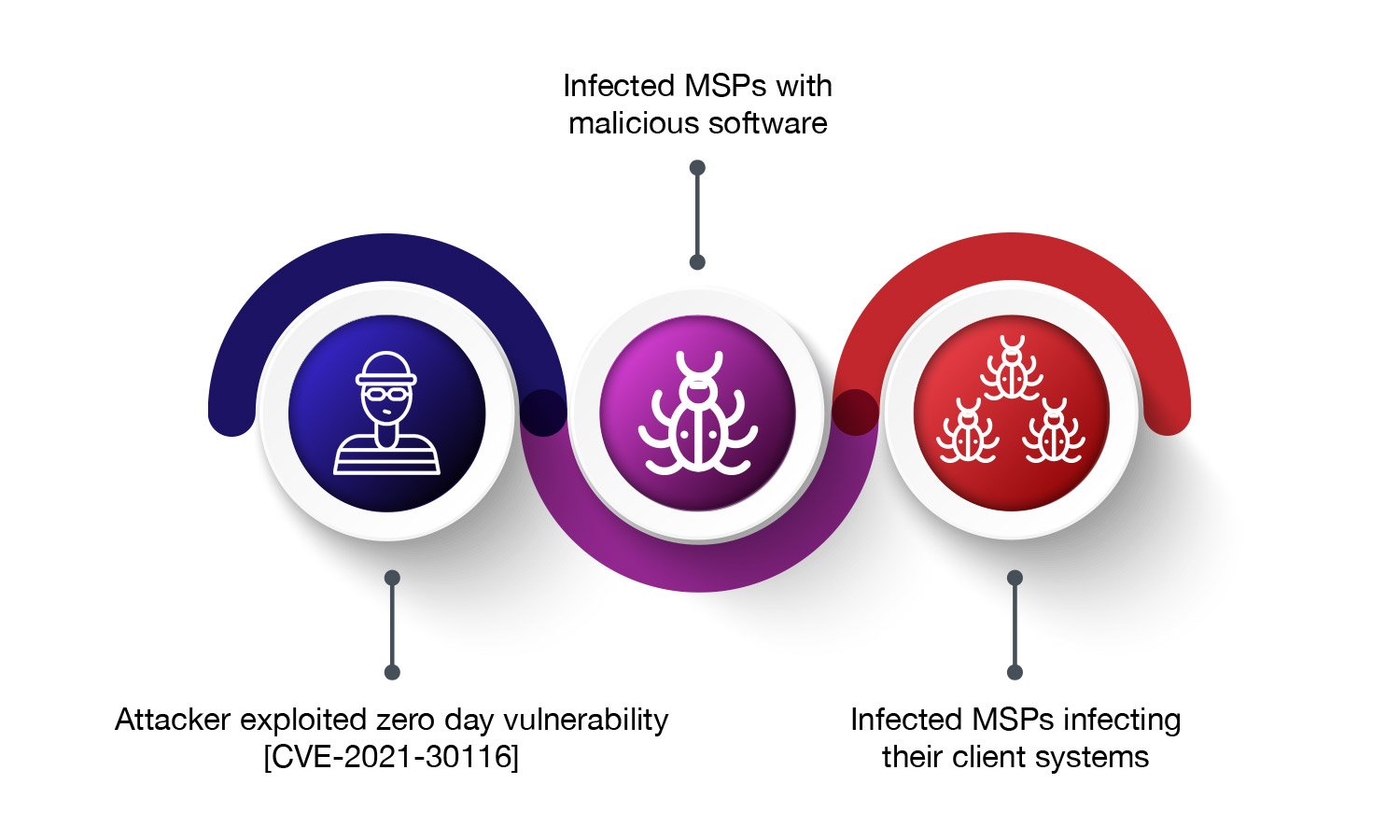
Speculations have suggested that the attack was yet another supply-chain ransomware attack. Multiple security firms and researchers have concluded that the attackers chose to exploit a zero-day vulnerability rather than tampering Kaseya’s codebase to distribute the malware. REvil/Sodinokibi ransomware threat actors were found to be responsible for the attack, exploiting a zero-day vulnerability to remotely access internet facing Kaseya VSA servers. Using this method, they hacked through less than 40 VSA servers and were able to deploy the ransomware to over a thousand enterprise networks.
What is Kaseya VSA?
Kaseya VSA, the Virtual System/Server Administrator is marketed as an endpoint management and network monitoring system that allows its client to have a unified remote monitoring and management platform. Users can perform functions such as remote controls to end-user computers, discovery and inventory on a client’s infrastructure, patch management to have a centralized system deploying software updates across all endpoints and monitoring and alerting of incident across the network. This makes it a convenient solution for MSPs to remotely manage their customer’s IT infrastructure and provide IT support and cybersecurity services to multiple enterprises. Kaseya VSA is also designed to have administrator rights provided down to all client systems.
In this incidence, an attacker had abused Kaseya VSA’s auto-update function and maliciously pushed the REvil ransomware onto Kaseya’s clients. This allowed the ransomware to reach to more victims, not only affecting Kaseya VSA customers but also the customers of MSPs that are using Kaseya VSA systems.
What Happened?
Various articles and researchers have concluded that attackers leveraged the standard VSA product functionality to deploy ransomware to the endpoint users. The attacker had exploited the zero-day vulnerability currently assigned the CVE-2021-30116 identifier.
The Kaseya zero-day vulnerability was discovered by Dutch Institute for Vulnerability Disclosure [DIVD] researcher Wietse Boonstra in early April, and had been shared with Kaseya prior to its exploitation in these ransomware attacks. Unfortunately, REvil attackers had managed to find the security flaw and attack by exploiting the vulnerability before Kaseya was able to issue or release a patch, resulting in this large-scale ransomware infection.
Given that the incident is currently in the middle of the investigation and patching stage, full details of the zero-day vulnerability “CVE-2021-30116” are currently not disclosed to the public. However, various research suggests that this vulnerability allows a remote non-authenticated attacker to compromise the affected system. To exploit this vulnerability, the attacker sends a specially crafted request to the affected application. Researchers have also concluded that the attacker managed to bypass authentication on the internet facing VSA web panel, exploit an arbitrary file upload, and execute commands via SQL injection on the VSA appliance.
Evidence of an executable code containing actions that would disable existing user sessions, remove IIS logs, and other cleanup activities has also been found. This attack appears to be geographically dispersed and the impact appears to have been restricted to systems running the Kaseya software.
The attack distributed its malicious payload in the form of a “Kaseya VSA agent hot-fix” launching the malicious software update package that targeted customers of MSPs and enterprise users of the on-site version of Kaseya’s VSA remote monitoring and management platform. The VSA appliance that had deployed a “Kaseya VSA agent hot-fix” package was observed to have bypassed antivirus solutions using an older and vulnerable version of the Microsoft Defender app, which it used to encrypt local workstations.
After compromising an MSP that utilizes Kaseya VSA, the attackers subsequently disabled the client’s administrative access to their respective Kaseya VSA platform, allowing the attackers to gain administrative access to all endpoints managed by Kaseya VSA. Upon gaining administrative access, the attackers were observed attempting to disable Microsoft Defender Real-Time Monitoring via PowerShell and deploy the ransomware.
REvil Ransomware
Various evidence, such as ransom notes dropped onto the infected systems, revealed that this cyber incident was closely tied with REvil/Sodinikibi ransomware group. The REvil ransomware group had also stepped forward to confirm associations with this attack after claiming the responsibility on its Dark Web leak site.
This is not the first time that the REvil ransomware group had topped news headlines. However, in this attack, REvil’s operators took a different approach in how they negotiate the ransom. REvil attacks can use multiple encrypted file extensions and typically will provide a decryptor that decrypts all encrypted extensions. In this attack, REvil demanded ransom payments made for each individual encrypted file extension found on a victim’s network, as opposed to their usual method of providing one decryptor to decrypt all encrypted file extensions.
The attackers are willing to provide a universal decryptor for victims of the attack, but only under the condition that they are paid $70 million in Bitcoin. The value has reportedly recently been lowered to $50 million.
REvil representatives have also responded to victims during the negotiation stage that in this attack, they had only encrypted networks and nothing more. Based on this information, it was suggested that REvil did not steal any victim’s data, which is typically what they utilize as a factor during the negotiation stage. This also indicates that the ransomware operation did not access the victim’s networks before the attack; however, it is still uncertain as to the extent of damage that was brought to the victim’s environment.
Riding the Waves
It is not a surprise that upon a new zero-day vulnerability disclosure or vulnerability being exploited by a cybercriminal group, other threat actors would take advantage of this opportunity and ride on the waves. Not long after the Kaseya attack, a new malspam campaign was observed containing various subject titles claiming to contain patch for Kaseya vulnerability. The attachment found in this malspam campaign appears to drop Cobalt Strike malware likely targeting users utilizing Kaseya products. Cobalt strike malware attachments appear to be the first malware that was found in the wild exploiting the current Kaseya situation.
MITRE ATT&CK
The following are the MITRE ATT&CK Tactics and Techniques associated with the Kaseya attacks:
| Tactics | Techniques |
| Resource Development | Obtain Capabilities: Vulnerabilities (T1588.006) |
| Resource Development | Obtain Capabilities: Exploits (T1588.005) |
| Initial Access | Exploit Public-Facing Application (T1190) |
| Execution | Command and Scripting Interpreter: PowerShell (T1059.001) |
| Persistence | Hijack Execution Flow : DLL Side-Loading (T1574.002) |
| Defense Evasion | Masquerading : Rename system utilities (T1036.003) |
| Defense Evasion | Impair Defences: Disable or Modify Tools (T1562.001) |
| Defense Evasion | Deobfuscate/Decode Files or Information (T1140) |
| Defense Evasion | Hijack Execution Flow: DLL Side-Loading (T1574.002) |
| Defense Evasion | Indicator Removal on Host: File Deletion (T1070.004) |
| Defense Evasion | Modify Registry (T112) |
| Defense Evasion | Subvert Trust Controls: Code Signing (T1553.002) |
| Impact | Data Encrypted for Impact (T1486) |
General Recommendations
Given that the vulnerability is newly discovered, there is still a lot of uncertainty about this attack and how it would affect clients utilizing Kaseya VSA software. As such, it is advised for clients utilizing Kaseya VSA software to have all on-premises VSA Servers to remain offline until further instructions from Kaseya on when it is safe to restore operations when a patch is made available to the public.
We strongly recommend to follow the guidelines by Kaseya, FBI and CISA if you use Kaseya VSA for your IT infrastructure and/or to reach out to your MSP if you are currently leveraging one for any IT-related management.
It is important to note that Proficio does not use Kaseya or any of its products. If you have questions, please do not hesitate to contact your Customer Success Manager or Security Advisor.