OVERVIEW
It’s no secret that phishing is one of the most common types of cyberattacks, both to individuals and organizations. According to the 2020 Verizon Data Breach Investigation Report, one out of four breaches involved phishing. So when Proficio’s Threat Intelligence Team received a client request, asking for assistance with a phishing incident, we conducted a thorough investigation on the specific threat actor. Below we share the key findings from our deep-dive investigation, including the hooks used and key targets for this campaign.
PHISHING CAMPAIGN DETAILS
The threat actor appears to be utilizing compromised user accounts within the targeted organization to send out phishing emails to internal contacts within their mailing list. We observed that such phishing emails sent by the legitimate, but compromised, user accounts would contain a download image that resembles the original PDF download button (Figure 1).

The Proficio’s Threat Intelligence Team dissected the email received, observing the below PCAP from a simulated access attempt against the download link (Figure 2). While the download button masquerades as an attachment, it appears to be a request URL link. The threat actor employs pretty standard social engineering “hooks” to creates a false sense of urgency with words such as “advise ASAP”. The purpose, of course, is to lure the victim into quickly clicking on the button without thinking too much.

Our analysis of the PCAP file (generated upon clicking on the download image seen from the email) reveals a redirect to an external request URL. Simulated access against the external request URL in a controlled environment reveal a redirect to a website with a “CLICK HERE TO VIEW” button. This phishing “hook” resembles a secure document intended for the victim to access.
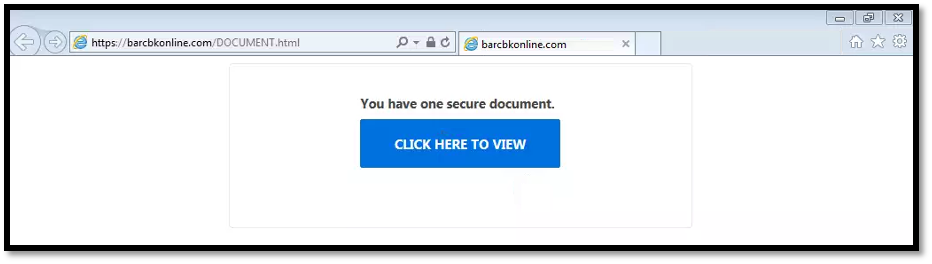
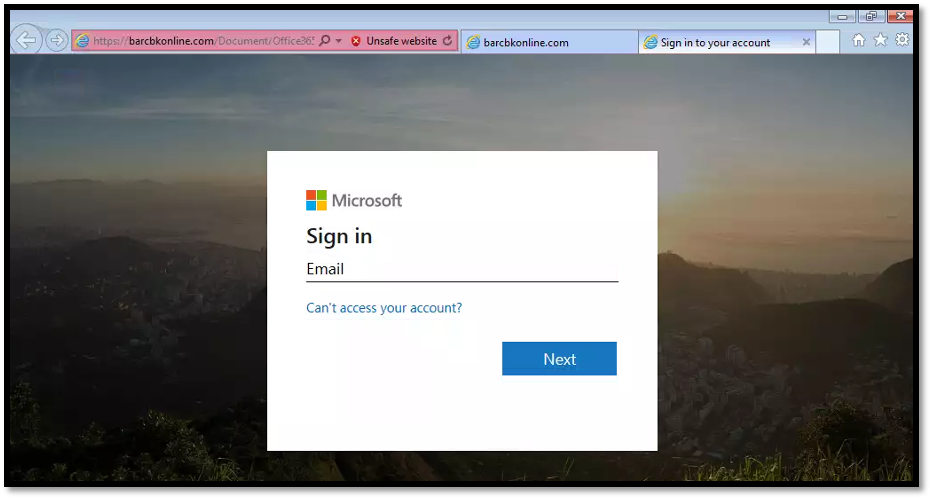
If a victim clicks on the “CLICK HERE TO VIEW” button, they would be directed to a fake Microsoft login page. When we input fake credentials into the login page, the adversary directs the user to an error page and requests for the credentials to be submitted again. We believe that the second credential request is meant to direct the user to the real Microsoft login page, a setup very similar to those practiced by other phishing campaigns. There are no other redirections observed subsequently.
DETECTION AND DISCOVERY EFFORTS
Proficio’s Threat Intelligence Team collected several different IOCs to identify potential access to the phishing sites. The IOCs includes known domain, IP addresses and unique URL parameter used in this phishing attempt.
Our investigation revealed that this campaign targets organizations rather than random individuals, as we observed that the phishing emails were sent to multiple employees within an organization together in one wave. Our analysis and study of the threat actor’s infrastructure and TTPs reveal that the threat actor conducting the phishing campaign appears to be interested in targeting specific geographic regions. We have identified the presence of several interesting strings such as “AUSTRALIA” and “YANKEE” used by the threat actor in their request URLs to organize their data depending on the geographic region associated with their target.
During our extensive investigations, we discovered the phishing emails were sent to multiple clients containing multiple different phished domains which ends with “/DOCUMENT.html”. Simulated access towards all the discovered sites exhibits the same redirection behaviour. Most of the identified activity was from inbound phishing emails. In most cases, we did not identify any click-through traffic that would indicate a potentially successful phishing attack.
While the threat actor appears to be interested in only a few geographic region, they do not appear to target any specific industry sector. We have identified multiple clients who have received emails from this phishing campaign. The sectors targeted by the threat actor most frequently were:
- Healthcare
- Commercial Services
- Real Estate
We will continue to keep an eye out for other phishing campaigns and intrusions that could be associated with this particular threat actor.
PRECAUTIONARY MEASURES & RECOMMENDATIONS
Phishing remains a popular attack vector because it continues to work very effectively. Anyone could receive phishing emails, and they could be sent by reputable or known users that were unknowingly compromised. It is advisable to take proactive steps to safeguard you and your organization to avoid being the next victim of a phishing attack or credential theft. We would recommend organizations to consider the following measures to protect themselves from phishing attacks.
- Educate your employees and users to improve cybersecurity awareness.
- Apply content filters on email gateways and email systems to prevent malicious content from reaching users and reduce the chance of a possible compromise.
- Educate users to report any suspicious emails received, even from other employees, to their cyber-security team.
- Always verify any suspicious emails through a different channel such as calling the supposed sender for verification.
- Quarantine emails sent from those compromised senders to anyone outside of an expected recipient list of filtering by email subjects if your organization is expecting legitimate emails from the senders.
- Reach out to any legitimate sender that appear have their account(s) compromised and instruct them to take action to secure their account(s).
- Make use of Multi-Factor Authentication to secure email and other user credentials
- Make use of network segmentation alongside the zero-trust model