OVERVIEW
In recent years, phishing campaign comes in different types and forms. The attackers are known to utilize free online tools and a variety of methods in hope to harvest credentials out from the victims.
On 16 August 2020, a relatively new spear-phishing campaign was detected which appears to utilize a free online tool – Typeform. The attacker created and hosted fake online forms to harvest victims’ credentials.
In this blog, we share some of the findings from our own deep-dive investigations into the attack activities that we have observed.
PHISHING DETAILS
Our investigation showed that victims would receive variants of emails, which can contain a URL link or an attachment that would redirect the victim to a phishing page. The phishing pages observed would inform the victim about a document that was sent through OneDrive in a PDF format.
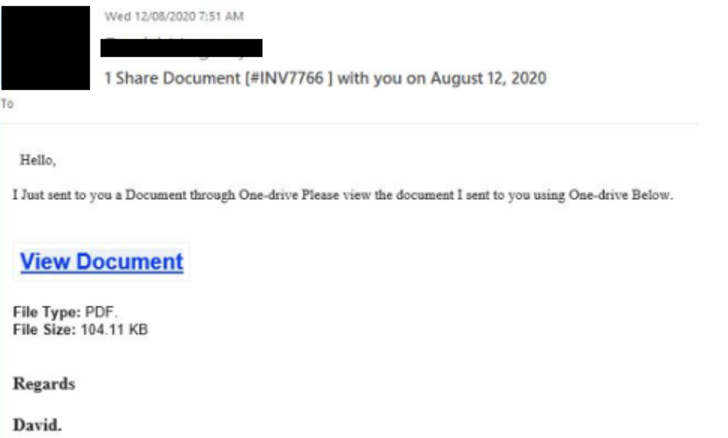
From our investigation, we have seen events where upon a successful phishing attempt, the compromised host would be used to subsequently broadcast the phishing email to all other employee using the organization email domain.
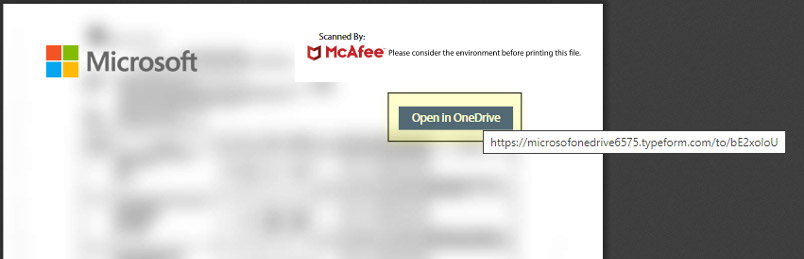
We have also seen events where the victim executed the phished PDF attachment in which the PDF would display a Microsoft labelled document with a “Open in OneDrive” button. Our investigation shows that clicking the button redirects to a phishing subdomain in Typeform with domain names such as
- “hXXps://document-signonline[dot]typeform[dot]com”
- ”hXXps://microsofonedrive6575[dot]typeform[dot]com”.
Further investigations by the team reveals interesting network behaviour. Upon successful access to the phishing site and the user starts filling the phishing form, the page loads the domain ending with the URL parameter “/start-submission”. The phishing form first prompts for the user’s email address and then their password. Once the credentials are filled in, a button is displayed for the user to click on in order to send the inputs and view a document on the website. Clicking the button loads the domain ending with the URL parameter “/complete-submission”. Observing this traffic would represent a complete cycle whereby the victim has accessed and provided the credentials to the phished sites.
DETECTION AND DISCOVERY EFFORTS
Proficio’s Threat Intelligence Team collected several different IOCs to identify potential access to the phishing sites. The IOCs include URL parameters and IP addresses.
The most notable indicator of accessing the phishing page was the sequence of redirections that occur after clicking the initial phishing link. Based on this, we were able to identify potential phishing attempts with higher certainty despite the limited visibility allowed for an MDRP/MSSP like Proficio.
From our investigation, this campaign appears to target by organization rather than random individuals, as we had observed the phishing emails being sent to multiple employees within an organization together in one wave. Even if the emails were blocked, there were no repeated attempts to send the emails to the targets. This campaign does not appear to target any specific industry sector.
PRECAUTIONARY MEASURES
This could have happened to anyone of us that works in any organization whom we would unexpectedly receive phishing email send by reputable or known users that were being compromised. It is advisable to safeguard you and your organization to avoid being the next victim from phishing attacks and credential theft. We would recommend organization to consider the following measures if this has seen within your environment.
- Educate your employees and users to improve cybersecurity awareness.
- Apply content filters on email gateways and email systems to prevent malicious content from reaching users and reduce the chance of a possible compromise.
- Educate users to report any suspicious emails received, even from other employees, to their cyber-security team.
- Always verify any suspicious emails through a different channel such as calling the supposed sender for verification.
- Quarantine emails sent from those compromised senders to anyone outside of an expected recipient list of filtering by email subjects if your organization is expecting legitimate emails from the senders.
- Reach out to any legitimate sender that appear have their account(s) compromised and instruct them to take action to secure their account(s).
- Make use of Multi-Factor Authentication to secure email and other user credentials
- Make use of network segmentation alongside the zero-trust model