OVERVIEW
On February 28th, the Proficio Threat Intelligence Team identified a new spear-phishing campaign that pretends to be sending a voicemail to targeted recipients.
In this blog, we share some of the findings from our deep-dive investigations into the attack activities that we have observed for this campaign.
PHISHING DETAILS
The attack starts with a phishing email pretending to send the recipient a voicemail. The email has a sender address starting with “voice@” and a subject containing text such as “New VM was sent” or “Voice Receiver”. The email contains a URL link which when clicked, redirects the recipient to a phishing page that resembles a Microsoft login page. The victim’s credentials are then stolen when entered and submitted on the fake login page.
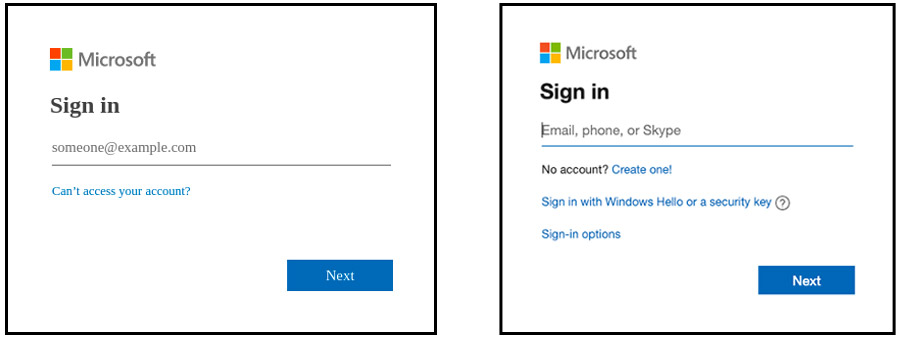
Figure 1 – An example of the fake login page (a) and real (b)
The initial phishing attempt is merely the first step of the adversary’s intrusion attempt. After successfully gaining user login, the threat actor responsible uses the credentials obtained to conduct a targeted spear phishing campaign against other employees within the victim’s organization.
DETECTION AND DISCOVERY EFFORTS
Proficio’s Threat Intelligence Team gathered and researched a number of different IOCs to identify potential access to the phishing sites. The IOCs included email subject strings, known domains, URL parameters and IP addresses. These IOCs were used to kickstart the detection and discovery phase of our threat hunting campaign. We identified several potential victims and performed deep-dive investigations on each potential victims identified.
The most notable and useful indicator we generated was the sequence of redirections that occurred after clicking the initial phishing link. Such activity strongly indicated a successful access attempt to the phishing page by the victim(s), and we were thus able to identify potentially successful phishing attempts with a high level of confidence despite the limited visibility of the dataset at our disposal.
Our investigations indicate that this campaign appears to focus on targeting organizations rather than random individuals, as we observed that the phishing emails were being sent to multiple employees within an organization together in a single wave. The adversary does not appear to be targeting any specific organization as there were no repeated attempts to send the emails to the targets even if the emails were blocked or did not result in a successful click-through.
No specific industry sector was targeted; we identified several victims of this campaign, all from different sectors:
- Banking and Financial
- Technology
- Commercial Services
- Real Estate
- Healthcare
All clients that we identified had a successful clickthrough activity of this phishing campaign have been notified. If you would like to know more about this campaign and what we have found, please reach out to your Client Success Manager or Security Advisor.
FUTURE PRECAUTIONARY MEASURES
Such phishing campaigns are not uncommon, and have been heightened in the past month where multiple phishing campaigns are using COVID-19 to lure victims. The use of COVID-19 as a phishing hook has been very effective in generating click-throughs for attackers’ phishing campaigns. To avoid being the next victim of credential theft, you can put into place safeguards to protect yourself and your organization from phishing attacks.
We would recommend the following measures:
- To improve cybersecurity awareness, educate your employees and users.
- To prevent malicious content from reaching users and reduce the chance of a possible compromise, apply content filters on email gateways and systems.
- If any suspicious emails are received, report them to your security team so they can notify other employees in the organization of the threat.
- Always verify such suspicious emails through a different channel.