Cyber attackers continued to successfully target organizations in all sectors and of all sizes during 2021. The biggest cyber attacks in 2021 resulted in damaging financial, reputational, and even societal consequences. Security leaders and teams should use the lessons learned from high-profile attacks to improve their organization’s security posture. Let’s look at 7 major cyber attacks in 2021 and the key lessons to learn from them.
The 2021 Cyber Attack Landscape
Threat actors continued to take advantage of additional security vulnerabilities created by the rapid pandemic-induced change to remote work. When remote work was a factor in data breaches during 2021, one study found the cost per breach increased by $1 million per incident.
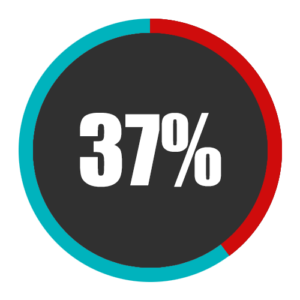 Ransomware remains one of the most significant cybersecurity threats with targets ranging from critical infrastructure to large enterprises to police departments. According to one report, 37 percent of organizations surveyed were hit by ransomware attacks in 2021.
Ransomware remains one of the most significant cybersecurity threats with targets ranging from critical infrastructure to large enterprises to police departments. According to one report, 37 percent of organizations surveyed were hit by ransomware attacks in 2021.
Ransomware gangs now regularly use double extortion techniques. Not content with just encrypting important files or endpoints, in double extortion attacks, adversaries exfiltrate sensitive data before delivering ransomware payloads. The added incentive to pay the ransom comes from the threat of sensitive data being published on the Dark Web.
Another worrying trend in several 2021 cyber attacks was a focus on disrupting or infiltrating supply chains. Malicious actors target supply chains because they know that the downstream effects can hit multiple organizations or even result in supply shortages of critical goods and services.
2021 Cyber Attacks That Shook the World
Bearing this landscape in mind, here is a run-through of seven high-profile incidents that made global media headlines.
1. Colonial Pipeline
The Colonial Pipeline 2021 cyber attack concerned the information security community, consumers, and government agencies. Colonial Pipeline transports diesel, jet fuel, and gasoline across a 5,500-mile journey starting in Houston and terminating in New York. In May 2021, an Eastern European ransomware group known as DarkSide managed to infiltrate Colonial Pipeline’s billing system.

Fearing an eventual lateral movement traversing the boundary between IT and operational technology (OT), the company halted all pipeline operations to contain the attack. The operational disruption lasted five days while Colonial Pipeline responded to the incident.
Part of the response involved paying a $4.4 million ransom to the ransomware gang. The FBI managed to recover a portion of this ransom in the aftermath. The concern around this breach was elevated by media images of panicked motorists queueing to stock up on gasoline because they feared an extended fuel shortage.
Subsequent investigations into the cyber attack on Colonial Pipeline found that the initial attack vector was a stolen password used to log in to a legacy VPN. The threat actors likely found the stolen password in a Dark Web leak list from a previous data breach. The Colonial Pipeline’s CEO, Joseph Blount, had to testify in front of the Senate Homeland Security and Governmental Affairs Committee about how the company handled this attack.
Lessons Learned:
- Multifactor authentication is critical: In his testimony, Mr. Blount said that the hacked VPN account only had single-factor authentication. In today’s threat landscape, depending on passwords alone to secure access to accounts is very risky.
- Poor password hygiene is still common: hackers used stolen credentials to log in to a VPN account. Aside from highlighting the vulnerabilities in relying on passwords, this attack shows how poor password hygiene, such as using passwords across multiple services and apps, remains commonplace. Better cyber awareness and training can combat this issue.
- 24/7 monitoring is key: detecting events like suspicious use of VPNs, credential abuse, and policy violations around the use of remote access applications helps prevent compromises.
2. Accellion
Accellion provides file sharing and team collaboration tools to organizations that are reported to include Morgan Stanley, Shell Oil Company, Kroger, Health Net, Stanford University, and many others. In December 2020 and January 2021, one of the company’s legacy tools, Accellion File Transfer Appliance (FTA), became compromised with multiple zero-day vulnerabilities exploited by UNC2546 and UNC258, two threat actors with links to the Clop and Fin11 ransomware gangs.
In healthcare alone, over 11 organizations were impacted by this supply chain attack. A zero-day attack is particularly challenging because it exploits previously unknown vulnerabilities for which no fix yet exists.
Lessons Learned:
- The importance of vulnerability management and patching: Speed is critical in patching zero-day vulnerabilities with known exploits. Risk-based Vulnerability Management tools and services can help organizations prioritize patch assets based on priority and context.
- The need for data exfiltration protection: In addition to double-extortion ransomware attacks, this supply chain attack demonstrated that threat actors see data exfiltration as the ultimate prize. It is important for organizations to detect precursors of data exfiltration and behavior anomalies and automate containment actions to prevent loss of data.
3. JBS
JBS is the world’s largest meat processor with reported annual sales of $50 billion and over 230,000 employees.
On Sunday, May 30, JBS USA discovered it was the victim of a ransomware attack that affected some of the servers supporting its U.S., Australian and Canadian IT systems. The company suspended all affected systems, then contacted law enforcement.
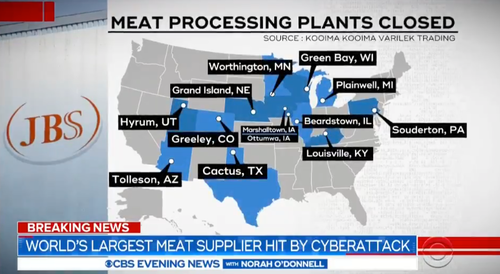
Assistance from the FBI helped to confirm that the prolific REvil ransomware operation was responsible for the JBS meat cyber attack. In a statement made to the media, JBS announced the payment of an $11 million ransom to REvil in an attempt to mitigate the risk of sensitive stolen data being published online.
Since the attack did not affect JBS’ backup data or core systems the company was able to recover from the attack in a few days with minimal disruption to the supply chain. JBS issued press releases on May 30, June 1, June 2, and June 3 to keep customers and the public apprised of the status of the incident.
Lessons Learned:
- Backup strategies still work: Some security commentators argue that backup strategies are redundant in a world where data exfiltration is the main goal of malicious actors. However, the ability to restore normal operations quickly after a cyber attack is imperative, particularly in critical industries such as meat processing upon which much of the world depends for survival. Just backing up systems and data is not sufficient. You also must take steps to protect your backup files from attempts to delete them.
- Early detection and response: More detailed investigations into the JBS attack found that data exfiltration began after leaked credentials were exploited as far back as February 2021. Early detection and response could have played a crucial role in thwarting attackers while they were in the network. Perimeter-focused controls are no longer sufficient for defending against attacks; security teams lacking internal resources can turn to managed detection and response.
- Incident Response Plan: Having a written Incident Response (IR) plan and routinely practicing the process makes a difference. JBS effectively engaged the appropriate government entities and third-party consultants who assisted with the forensic and mediation work.
4: Brenntag
In April of 2021, Brenntag, a German chemical distribution company, became yet another victim of DarkSide ransomware. Brenntag employs more than 17,000 people worldwide, and the company reported over $14 billion of revenue in 2019.
 In yet another double extortion attack, DarkSide managed to exfiltrate 150 gigabytes of data from the North American division of Brenntag’s network. After data exfiltration, the Brenntag ransomware payload encrypted multiple devices and files on the company’s network using the Salsa20 file encryption algorithm.
In yet another double extortion attack, DarkSide managed to exfiltrate 150 gigabytes of data from the North American division of Brenntag’s network. After data exfiltration, the Brenntag ransomware payload encrypted multiple devices and files on the company’s network using the Salsa20 file encryption algorithm.
The immediate response to the Brenntag ransomware attack focused on containing the threat by disconnecting affected systems from the network. The company also paid a $4.4 million ransom in return for both a decryption key and not having sensitive data belonging to 6,700 individuals published online. The sensitive data included birthdates, Social Security Numbers, driver’s license numbers, and health data.
Credential theft appeared to play a prominent role in this attack. A ransom note seen by security researchers at Bleeping Computer alluded to the fact that threat actors “bought access to the network”.
Lessons Learned:
- Stolen credentials are a big problem: Initial network access via stolen credentials was a common theme in several 2021 cyber attacks. Mitigation requires a multi-pronged approach that includes multi-factor authentication, ongoing cyber education, and regularly mandating password changes.
- The paradox of cyber attacks: Threat actors often deploy sophisticated tools and techniques to evade detection once inside networks, however, the methods they use to gain initial access often exploit incredibly basic cybersecurity flaws.
5: Volkswagen and Audi
Volkswagen has consistently been one of the top-selling automotive brands. In June 2021, details emerged of a significant data breach both at Volkswagen and Audi, one of the Volkswagen Group’s luxury line of vehicles. The breach exposed information belonging to 3 million customers.
For the majority of customers, the leaked details were basic and non-sensitive. However, at least 90,000 people were contacted about sensitive data exposure, including driver’s license numbers, Social Security numbers, and dates of birth.
A spokesperson indicated the Volkswagen data breach stemmed from a compromise at a third-party vendor used by the company. Vice magazine reported that a hacker obtained the data by scanning the Internet for unsecured Microsoft Azure Blobs, which are used to store unstructured data in the cloud.
Lessons Learned:
- Third-party risks: Volkswagen trusted another vendor with its valuable customer data, but that same vendor failed to implement such a basic practice as securing all data stored in the cloud. Third-party risk management is crucial to avoid breaches like this one.
- The need for data visibility: You cannot protect sensitive data when you do not know where it is stored or how it is secured. Comprehensive data visibility may have mitigated the possibility of this Volkswagen data breach from happening.
6: HSE Ireland
The Health Service Executive runs Ireland’s public health system. Over 67,000 direct employees help to maintain the health of Ireland’s populace. Several severe Covid-19 outbreaks stressed Ireland’s health system in 2021, and a ransomware attack in May came at the most unwelcome of times.
The installation of a ransomware payload by Conti threat actors completed a two-month operation that severely impacted the HSE’s IT infrastructure. The immediate aftermath of the HSE cyber attack resulted in healthcare professionals losing access to IT systems, including patient information systems, clinical care systems, and laboratory systems.
Equally as severe as this disruption to important health services was the exfiltration of sensitive healthcare data belonging to 1,000 patients. During negotiations about a ransom, Conti gang members began leaking patient data for up to 520 individuals on the Dark Web.
A detailed incident report found that the HSE cyber attack started in March 2021 when an employee clicked and opened a malicious Excel attachment. This attachment provided remote access to the HSE’s IT environment. Threat actors used Cobalt Strike, a penetration testing tool, to escalate their privileges on the originally compromised workstation.
Lessons Learned:
- The need for threat intelligence: Robust threat intelligence and discovery helps detect tools like Cobalt Strike and stop similar incidents in their tracks.
- The danger of phishing: Phishing emails with malicious attachments provide low-hanging fruit for adversaries to infiltrate your network. Robust email security software and employee training reduce the risk of malicious attachments or users being enticed to visit infected websites.
7: CNA Financial
Last but not least in our overview of 7 of the major 2021 cyber attacks is an attack that resulted in one of the largest ransom payments. CNA Financial, one of the biggest insurance companies in the United States, was hit by a March 2021 ransomware attack that encrypted up to 15,000 systems. The threat actors used a ransomware strain known as Phoenix CryptoLocker.
The attack began when an employee downloaded a fake browser update from a genuine website onto his/her workstation. Additional malicious activity helped to elevate privileges from the workstation to get network-wide administrative access. The final ransomware payload took down so much of the company’s IT infrastructure that executives felt they had no other option but to pay for the decryption key. The $40 million CNA Financial ransom payment set a record at the time that remains today.
- The value of detection and response capabilities: With seemingly no functioning backup strategy in place to restore encrypted devices and files, this incident underscores the value of detection and response capabilities. By emphasizing defense-in-depth, businesses can detect and respond to cyber attacks much faster and limit their effects.
- Some companies still pay: Despite government admonitions against paying ransom demands, several large companies paid substantial sums to hackers in 2021; none were more substantial than the $40 million that was the CNA Financial ransom. It is recommended that IT leadership prepares for this possibility by discussing options with management and their cyber insurance provider.
2021 Cyber Attacks Conclusion
There are many lessons to take forward from this list of seven major cyber attacks in 2021. Basic security flaws can provide hackers with an easy route into networks; even those belonging to the largest enterprises with the highest security investments. Despite the ease of initial entry, a common thread here is that detection and response capabilities are critical to detecting and preventing breaches.
Businesses stand to gain a far more robust security posture by investing in managed detection and response (MDR). Ready-made expertise in threat intelligence, detection, and response awaits businesses that allocate some of their security budget to MDR services.
Contact Proficio today to see how our leading MDR solution helps businesses like yours defend against cyber threats.
