Cyber Exposure Monitoring and Identity Threat Detection and Response: A Powerful Combination to Protect Organizations

Combining Cyber Exposure Monitoring (CEM) with Identity Threat Detection and Response (ITDR) is a strategic approach to improving organizational cybersecurity. The data shared from Proficio’s experience over the past 12 months underscores how dangerous compromised credentials can be, particularly as a growing percentage of critical cyber incidents stem from credential compromises. Key Highlights The Increasing Threat of Compromised […]
Gen AI Operationalized in a Global SOC Leads to a 34% Increase in Productivity and Enhanced Incident Fidelity

Gen AI Operationalized in a Global SOC Leads to Productivity Can Generative AI be used in cybersecurity? Admittedly, we were skeptical that Generative AI was ready to help us in our SOC operations for threat detection and response. We’d heard all the vendor hype, but no one had any examples of real success. So, we […]
Breach and Attack Simulation: Elevating Cybersecurity Defense
In an era of increasingly complex cyber threats, organizations are constantly under threat from sophisticated cyber adversaries. To stay ahead, it’s crucial to not only identify and respond to incidents but to proactively test and validate your defenses. Breach and Attack Simulation (BAS) has emerged as a critical tool in this proactive approach. Why Breach […]
AI Cybersecurity | Why Singapore Businesses Should Use It
Did you know that 96 percent of Singaporean businesses have reportedly suffered a data breach? And cyber-crime is not slowing down. With the financial risk from cyberattacks estimated to be US$5.2 trillion between 2019 and 2023, it creates an ongoing challenge for investors, corporations, and consumers around the world. In Singapore, experts detected approximately 4.66 […]
Benefits of Integrated Vulnerability Management with Managed Detection and Response in Strengthening Cyber Resilience
In the contemporary digital environment, organizations face an increasing number of sophisticated cyber threats. This emphasizes the need for an integrated approach in cybersecurity measures combining vulnerability management with managed detection and response (MDR) services. The combination aims to not only identify vulnerabilities but also ensure timely responses to potential threats, thus enhancing an organization’s […]
The Impact of AI on Endpoint Detection and Response
In the dynamic realm of cybersecurity, Endpoint Detection and Response (EDR) services leverage Artificial Intelligence (AI) to revolutionize threat detection, response, and prevention. This article explores how AI-driven EDR services fortify organizational defenses against cyber threats. AI-Powered Threat Detection AI algorithms enable EDR services to analyze vast amounts of endpoint data in real time, […]
DoppelPaymer Ransomware
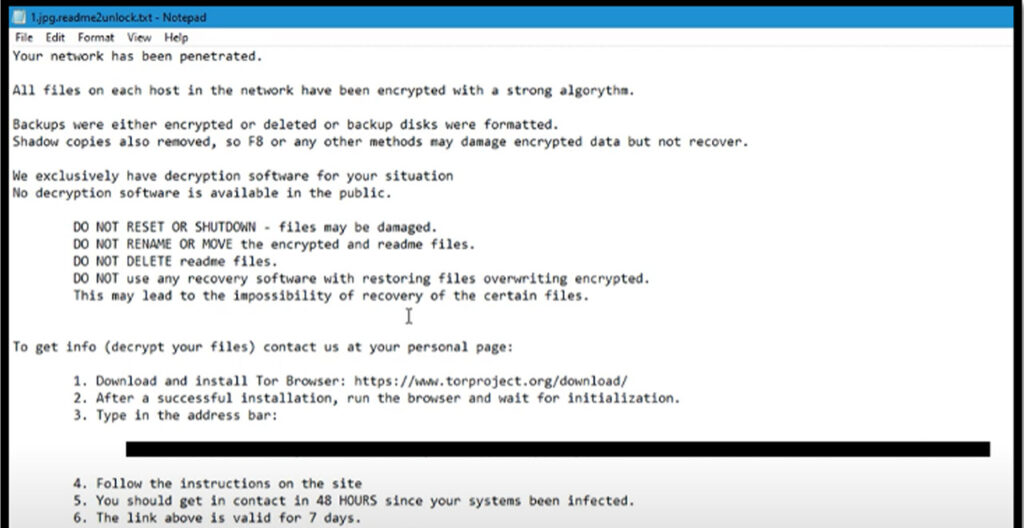
Overview – What is DoppelPaymer? Recently, Proficio’s Threat Intelligence Team has observed a surge in ransomware cases that take advantage of the current COVID-19 situation. In this blog, we will discuss a variant of ransomware named “DoppelPaymer”, which has significantly raised its popularity over the last month, and provide additional details discovered during our research. […]
Data Breaches and the Dark Web: Protect Your Organization
Data breaches are a formidable challenge in the digital age, posing severe risks to organizations of all sizes. These breaches occur when unauthorized individuals gain access to private data, often resulting in substantial financial, reputational, and legal repercussions. They can stem from various sources, including cyber-attacks, human error, or inadequate security protocols. In this interconnected […]
Operationalizing Your SOC: Navigating Cybersecurity Challenges
Organizations of all sizes face increasing challenges in securing their networks and sensitive data due to the relentless growth of information and the surge in cyber threats. Despite having effective security tools, a recent study conducted by Sapio Research with 2,000 IT security analysts reveals that three-quarters lack complete visibility into their environments. This blog […]
Proficio Continues Advancing the Global Mission of MDR with ISO 27001:2013 Certification
I am thrilled to share a momentous achievement for Proficio – the successful attainment of the ISO 27001:2013 certification. This isn’t just any certification; it’s the gold standard in information security – emblematic of our dedication to upholding the highest international standards for data protection for our company and our MDR clients across the globe. […]
Guarding Against Social Engineering Scams During the Holidays: A Primer from the Proficio Cyber Exposure Monitoring Team

The holiday season brings a spike in social engineering scams, leveraging the festive atmosphere to manipulate individuals into divulging sensitive information. Proficio’s Cyber Exposure Monitoring team emphasizes the importance of being vigilant during this high-risk period. This article serves to educate users on recognizing these scams, understanding their impact on organizations, and adopting strategies to safeguard personal and professional data.
Phishing Prevention: How to Identify and Avoid Cyber Threats

A global effort must be made to help ensure everyone stays safe and protected when using technology whenever and however you connect. As Cybersecurity Awareness Month comes to a close, we want to leave you with a recap of what social engineering is, how the threat actors operate and how to spot a social engineering […]